
Password Management: How to Create and Store Strong Passwords for All Your Online Accounts
Creating strong, unique passwords for each online account is crucial to prevent hacking and data breaches. This article highlights the importance of password complexity, unpredictability, and regular updates. It recommends using password managers to store passwords securely and enabling two-factor authentication for added protection. Avoid weak, common, or reused passwords across accounts.
Read More
Cloud Storage Security: Safely Storing and Sharing Files in the Cloud
Cloud storage services like Google Drive, Dropbox, OneDrive, and iCloud allow easy access to files from any device but require strong security practices. Key risks include account hacking, improper sharing, data breaches, and unsecured networks. Best practices for security involve using strong passwords, enabling 2FA, encrypting files, managing permissions, and avoiding public Wi-Fi.
Read More
Mobile Payment Security: How to Protect Your Financial Information with Mobile Payment Apps
Mobile payment apps like Apple Pay and Google Pay offer convenient, secure transactions but are still vulnerable to cyber threats. This article explains their operation and associated risks such as device theft, phishing, and fake apps. It also provides best practices for protection, like enabling biometric authentication, using strong passwords, and avoiding public Wi-Fi.
Read More
How to Secure Your IoT Devices: Protecting Your Smart Home from Cyberattacks
The Internet of Things (IoT) improves daily convenience but poses cybersecurity risks. Common issues include weak default passwords, unsecured network connections, outdated software, and data privacy concerns. Best practices for securing IoT devices include changing defaults, using separate networks, updating software, and monitoring activity. Protecting IoT devices helps safeguard personal data and home security.
Read More
Cybersecurity for Remote Workers: Protecting Your Data and Devices While Working from Home
As remote work increases, strong cybersecurity becomes crucial due to unique risks such as unsecured networks, personal device vulnerabilities, and phishing attacks. To protect data and devices, remote workers should use VPNs, enable MFA, keep devices updated, secure home networks, avoid public Wi-Fi, and follow company-approved tools.
Read More
Email Security: How to Protect Your Email Accounts from Hackers and Phishing Attacks
Email is a vital communication tool but also a prime target for cybercriminals. This article discusses common threats like phishing, account hacking, spoofing, and ransomware. It offers tips to secure your email, such as using strong passwords, enabling two-factor authentication, and being cautious with links and attachments. Stay vigilant to protect your information.
Read More
Online Shopping Security: How to Shop Safely and Avoid Scams
Online shopping is convenient but comes with risks like cybercrime and fraud. Common scams include fake websites, phishing emails, and non-delivery schemes. To shop safely, use trusted websites, secure payment methods, and avoid saving payment details. Monitor your accounts for suspicious activity and report any fraud immediately.
Read More
Understanding Social Media Security: How to Protect Your Accounts and Personal Information
Social media platforms are essential in personal and professional lives yet come with security risks like identity theft and phishing. Protecting accounts involves using strong passwords, enabling two-factor authentication, monitoring for suspicious activity, and limiting personal information shared. These measures help reduce risks and maintain privacy and security.
Read More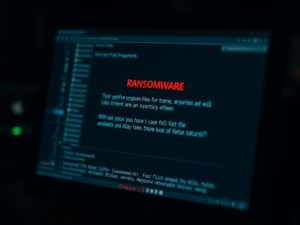
Understanding Ransomware: A Modern Cyber Threat
Ransomware is a type of malware that encrypts victims’ files, demanding payment for decryption. Originating in the late 1980s, it has evolved significantly, notably with CryptoLocker and WannaCry. Sophisticated tactics, including double extortion, pose serious threats to individuals and organizations. Prevention includes regular backups, software updates, and cautious email practices.
Read More
Recognizing and Preventing Insider Threats: Protecting Your Business from Internal Risks
Insider threats, often overlooked, pose significant risks to businesses through data breaches, financial losses, and reputational damage. They can be malicious or unintentional and stem from employees, contractors, or partners. Recognizing warning signs such as unusual access patterns and implementing preventative measures like role-based access control, employee training, and multi-factor authentication are crucial strategies for minimizing these risks.
Read More